MSc Project: Cyber Security
MSc Project title: Analysing risk in Vulnerability Assessment and Penetration Testing Methodology
Course: MSc Cybersecurity and Digital Forensics
Introduction/rationale:
The motivation behind choosing the project stemmed from the growing need for more structured and standardized approaches to penetration testing and vulnerability assessment. With cyberattacks becoming increasingly sophisticated, organizations struggle to identify and remediate vulnerabilities efficiently.
| TECH TERM: Penetration testing, often referred to as ‘pen testing‘, is a cybersecurity practice where ethical hackers simulate cyberattacks on a computer system, network, or web application to identify vulnerabilities that could be exploited by malicious hackers. The main goals of penetration testing is to: 1. Identify security weaknesses 2. Assess the effectiveness of security measures 3. Improve overall security posture: By identifying and fixing vulnerabilities, organizations can strengthen their defenses against potential cyber threats. |
The MITRE ATT&CK Framework provides a well-defined structure for understanding adversarial techniques and tactics, making it ideal for enhancing VAPT (Vulnerability Assessment and Penetration Testing) methodologies. This project aimed to leverage MITRE’s capabilities to analyze risk, improve testing scope, and ensure that testing efforts are comprehensive and aligned with real-world threats.
Project overview:
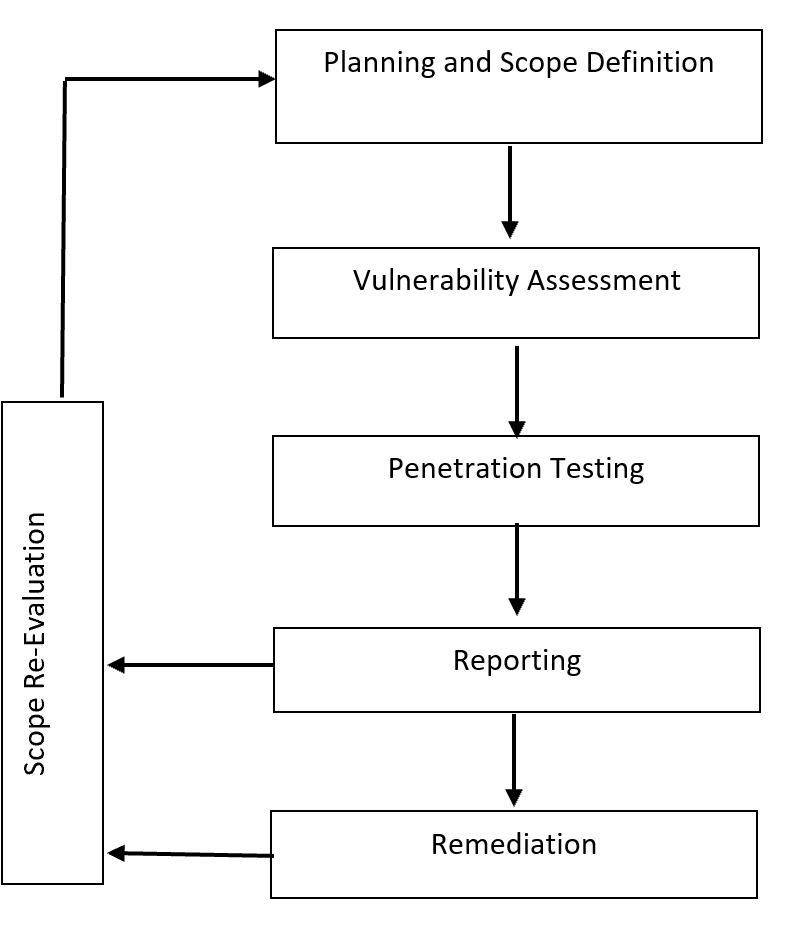
In this project, we integrated the MITRE ATT&CK Framework into the traditional VAPT methodology to refine the testing scope and increase effectiveness in detecting vulnerabilities. The steps involved included:
- Defining the Scope: The project began by clearly defining the boundaries and goals of the penetration test. Using the MITRE Framework, specific attack vectors and techniques relevant to the organization’s environment were identified.
- Conducting Vulnerability Scanning: Automated tools were used to perform initial vulnerability scans, identifying weak points that attackers might exploit.
- Simulating Attacks Using MITRE Tactics: We designed attack scenarios based on the tactics and techniques outlined in MITRE ATT&CK, simulating adversarial behavior. This allowed us to target the actual risks that real attackers would exploit, rather than theoretical vulnerabilities.
- Analyzing Results and Refining Scope: Post-attack analysis identified network gaps and weaknesses in current defenses. The scope of the testing was iteratively refined based on these findings.
- Reporting and Remediation: Finally, comprehensive reports were generated, providing actionable insights for the security team, along with specific recommendations for closing vulnerabilities.
Visual Representation: A flow diagram illustrating the process of integrating MITRE with VAPT in Penetration Testing Stages, is located below:
Project outcome & conclusion:
The integration of the MITRE ATT&CK Framework significantly enhanced the scope and depth of the VAPT process. By aligning testing activities with real-world adversarial tactics, the project was able to identify previously overlooked risks and vulnerabilities. The methodology provided a more focused, risk-based approach to penetration testing, ensuring that organizations could better prepare for and mitigate threats. The project demonstrated that using MITRE not only strengthens the identification of vulnerabilities but also offers a more comprehensive understanding of the adversarial techniques that could affect critical systems.
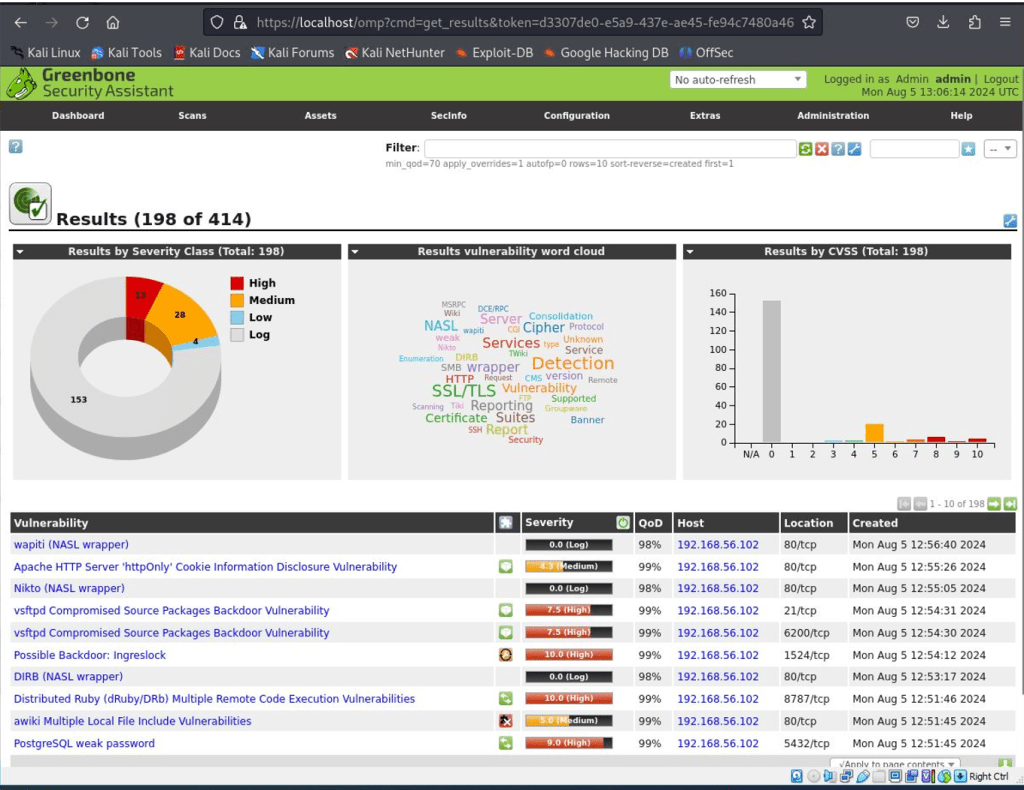
OpenVAS is a full-featured vulnerability scanning tool, that was used for this purposes of this project. An example output of vulnerability findings can be seen below:
Q. What Career and job role are you hoping to move into after graduation?
After graduation, I am hoping to pursue a career in cybersecurity, with a specific focus on roles like:
- Penetration Tester: Using tools and methodologies (such as MITRE ATT&CK) to identify vulnerabilities in an organization’s IT infrastructure.
- Cybersecurity Analyst: Monitoring, analyzing, and defending against cybersecurity threats.
- Security Consultant: Advising organizations on how to improve their security posture by implementing effective VAPT practices.
These roles align with my passion for understanding and mitigating cyber risks, particularly in offensive security and ethical hacking.
Q. Please share a top tip/advice for students who are interested in completing a University Degree?
My top tip for students is to focus on practical applications of what you learn. Theoretical knowledge is important, but real growth happens when you apply it in real-world scenarios, whether through internships, projects, or labs. Hands-on experience not only solidifies your understanding but also makes you more marketable in the job market.
For further information about Computing courses at UWTSD, please click-here.
~