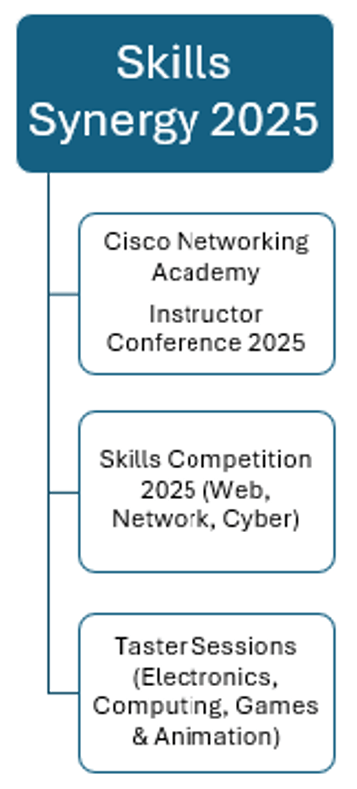
Graduate profile: Dale Warner
Graduate profile for Dale Warner, a Solutions Engineer at Cisco.
"Exposure to new and challenging events is critical. Everyone is winging it; no one can know it all."
"Creativity requires play, and play can be messy. Embrace the cluttered desk!"
"My days can range from face-to-face customer meetings across the UK, building high level plans/designs/BoMs from my home office, or turning my time to study so I can stay on-top of the latest technology trends."
Q. Name: Dale Warner
Q. What was your university course: BSc (Hons) Computer Networks
Q. Job title and role? Solutions Engineer at the Central Government Team at Cisco
Q. Briefly describe the organization you work for? Cisco are the market leader when it comes to networking. They also provide cutting edge technologies and services across a wide range of areas; Security, collaboration, observability, to name a few.
Q. Which skills learned at university are helpful to you in your job? While at university the most important skill I learned was how to concisely present a complex idea or solution. Being able to do so allows me to talk and explain new products and ideas to customers, cutting out all the unnecessary fluff.
Q. A typical day and how would you describe it? Like any engineer, two days are very rarely the same. But I talk with customers about their technical issues and look to provide Cisco solutions to bridge the gap. This requires me having a board understanding of a range of technologies and where/how Cisco products can be used. My days can range from face-to-face customer meetings across the UK, building high level plans/designs/BoMs from my home office, or turning my time to study so I can stay on-top of the latest technology trends.
Q. What aspects of your job do you enjoy most? I enjoy meeting customers, understanding their needs, and proposing suitable solutions. This, alongside learning on the latest technologies and having a future vision of the technology industry.
Q. Advise for students who would like to start a Career? It’s okay not to have an end goal, so long as you know what you want to do next. When your end destination isn’t set you can put all your effort into achieving your next goal. Exposure to new and challenging events is critical. Everyone is winging it; no one can know it all.
Q. A quote that you like / live by / inspires you?
My favorite quote is a quip from Albert Einstein “if a cluttered desk is a sign of a cluttered mind, of what, then, is an empty desk a sign?” I’d like to add – creativity requires play, and play can be messy. Embrace the cluttered desk!
Thank you for your profile Dale, it will help to inspire current and future students.
We are most grateful. We hope to see you at future alumni events.
Well done and Congratulates on your success Dale.
Da iawn a llongyfarchiadau Dale
~